5 Ways Biometric Security Will Redefine Mobile Phone Authentication
The following is a guest post submitted to M2SYS by Nasrullah Patel
You may be aware of the term “biometrics” – an evolving technology used for identity authentication and access privilege. The word biometrics is derived from the Greek language where bio stands for life and metrics for measure. Biometric security technology was first made commercial in the year 1970. It has become intrinsic for almost all security technologies ranging from government and military standpoints to private organizations, healthcare, and the telecom sector.
Mobile devices play a significant role in everyday life, not only for communicating with others but also used for entertainments and social relationships. Along with the increase in the usage of mobile devices like smartphones, tablet PCs, laptops, and other portable devices, the growth of confidential data like (bank accounts, personal and official e-mails, photographs, video) that these mobile devices store is also increasing. Currently, biometric security is one of the best authentication solutions to raise security within the mobile environment and there are plenty of examples of integrating biometric technology via Mobile App Development that includes; mobile voting, banking, and performing online transactions.
Biometric technology performs individual authentication based on the physiological characteristics like (fingerprint, palm veins, face, DNA, palm print, hand geometry, iris identification, retina and odour/scent) or behavioral characteristics like typing rhythm, gait, and voice.
Biometric security systems can replace the traditional method of entering passwords or PINs with a swipe of a finger so that the phone can be unlocked and used. Biometric methods embedded in mobile phones include fingerprint recognition, face recognition, signature recognition, voice recognition, and iris Recognition. Let’s take a look at the methods of biometric authentication in mobile phones:
Fingerprint Recognition:
AuthenTec is a global leader in providing fingerprint recognition systems. The AuthenTec suite includes five technologies:
- TruePrint captures the fingerprint image from the five layers of skin beneath the surface. This reduces the risk of not acquiring a fingerprint because the skin-surface has wearied.
- TouchStone It is used to create waterproof sensors.
- TrueFinger It ensures that only fingerprints are read.
- TrueNav It tracks the motion of the finger on the sensor, and it is translated in the move of a cursor on the screen.

Pantech was the first manufacturer to embed fingerprint scanning technology on its GI 100 mobile phone. Lenova used integrated fingerprint security in its P960 phone to protect sensitive information such as VIP recordings, address book, call log, and text messages. Fujitsu introduced first waterproof fingerprint-enabled mobile phone. AuthenTec agreed to a 356 million dollars acquisition offer from Apple.
Read More: Will Biometric Technology Take Over Banking Security?
Face Recognition:
ClassifEye and Omran developed face recognition technology in camera-enabled mobile phones. The advantage of this technique is that it does not require installing any additional hardware or software because cameras already exist in most phones today. The minimum camera resolution should be 100,000 Pixels.
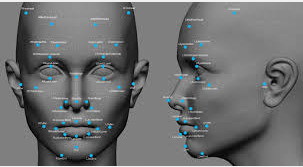
Sharp has also integrated face recognition technology in mobile phones. To unlock the mobile phone, it has to match the user’s face captured by a camera against a saved image portrait.
Voice Recognition:
Voice is the only available biometric identifier that can be used over the telephone. Customers will become impatient if a number of security questions is asked before authentication. Therefore voice biometrics provides a quick reply to the agent to ensure that the person is who they claim to be without a long wait time. It is cheaper and can be integrated into existence Interactive Voice Response Systems (IVRs). Mobile voice biometric systems ensure reliability, security, and provide a seamless user experience since it uses voice prints that are unique to each customer.

One of the India’s largest private sector banks (ICICI Bank) deployed voice recognition biometrics which authenticates the customer based on their speech patterns and allows them to perform transactions through the call centre.
Signature Recognition:
Dynamic signature analysis depends on the manner in which a signature is written and not on the physical appearance of the signature. When PDA users sign their name multiple times attributes such as pressure, direction, or velocity are recorded during the subscription.
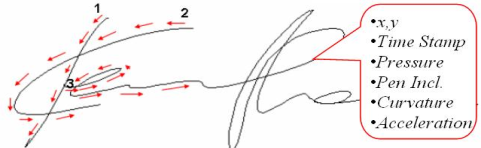
Iris Recognition:
The first smartphone (Arrows NX F-04G) with iris recognition biometrics was developed by Fujitsu. The unique pattern of the iris is used for individual identification through a photograph of your eye and used as a password for ensuring enhanced security.

A German computer hacker recently demonstrated that it is easy to foil biometric fingerprint security by using commercial software and a couple of photos of one’s hand.
Read More: 5 Factors to Consider in Choosing the Best Biometric Modality
The aforementioned biometric security systems for mobile phones are not only making the mobile phones tauter, but they are also making the usage of cell phones easier and even more entertaining.
The onus is on cell phone manufacturers to ensure consumers are comfortable with using biometrics on their mobile phones via the best Mobile App Development Companies. “People are wary of the fingerprint and the eyeball scan”, said David Kane, CEO of global security company Ethical Intruder, warning against solely depending on biometrics.
Author Bio: Karan Dave is a content developer with one of the top ios App Development Companies, Peerbits. He is IT graduate with Masters in Mass Communication. Being a tech geek, he keeps a close watch over the industry focusing on the latest technology news and gadgets.












Really a great information you have to shared. Thanks. https://goo.gl/K31MVW
Thanks, this is a great list. I’m now following around half the folks I’ve commented on – so for me this has been a double win – the comment and the further reading material that helps me and my blog!
I respect your work, regards for all the interesting blog posts.
I agree with you
How do you delegate an important assignment to others while ensuring that it will be completed successfully?
very nice! that much of the information you provided through this article thanks for sharing this
good to read. Thanks for sharing
Great blog, I do think technology is ever-evolving and there will always be new methods for mobile applications security.
Competent and accessible, but I think you missed quite a lot of details, try to reveal them in future posts
Thanks you and I admire you to have the courage the talk about this,This was a very meaningful post for me. Thank you.
This is a mind blowing, thanks for sharing. help me a lot.
Thank you for sharing just a great information.
Thanks for sharing. Useful
What a fantastic post! I love to read this topic you made, very ingenious. I would love to read more informational posts about Best mobile app development company.
Thanks a lot for sharing the blog. the information you shared is just awesome and very helpful.
Thanks for sharing informative information with us, Keep sharing
the blog is very infomative one.
Facial biometrics is one of the most convenient option for mobile phone authentication. Other options include fingerprint recognition, iris recognition, and voice recognition. Each method has its own advantages and disadvantages, such as security, and privacy. Ultimately, the best option will depend on the specific needs and preferences of the user, but in my sense facial biometrics is the most convenient one.
hi, thanks for sharing this informative post.