Black Hat Iris Biometrics Attacks Don’t Tell The Whole Story

Planet Biometrics released an article today “Iris attacks no surprise to iris recognition inventor” which details an interview with John Daugman, Professor of Computer Vision and pattern Recognition at Cambridge in response to the recent Black Hat conference paper that hacked into an iris system and re-engineered images to fool a recognition device. Professor Daugman is credited with developing and patenting the first algorithm for iris recognition which is still widely used across the world.
Professor Daugman acknowledges in the article:
“This is a classic ‘hill-climbing’ attack that is a known vulnerability for all biometrics….the vulnerability in question, which involves using an iterative process to relatively quickly reconstruct a workable iris image from an iris template, is a classic “hill-climbing” attack that is a known vulnerability for all biometrics.”
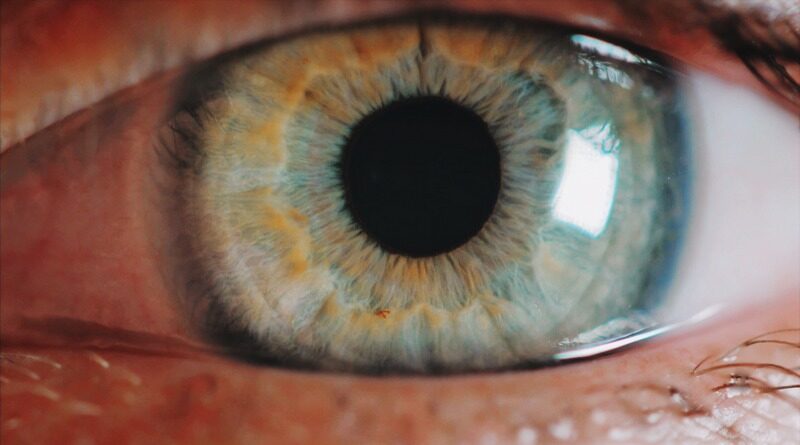
The primary vulnerability in the Black Hat conference paper was the full disclosure and access to the Iris Code template, as well as having the ability “to generate an IrisCode template from an image, and to do so repeatedly and iteratively.” In other words, without access to the encoding algorithm or to a hardware device that implements it, the “attack” would not have been possible. Be that as it may, the Black Hat scientists did have access to the encoding algorithm but not all iris biometrics algorithm research and developers give access to the Software Development Kit (SDK) that is needed in order to perform the “attack.”
According to Daugman, this should be a sign, “to maintain cryptographic security on IrisCode templates” to maintain the highest level of security and thwart would be system attacks. Daugman went on to say that in addition to cryptographic security, there is also the issue of iris hardware detecting an artificial iris vs. a real one. Most of the higher quality iris biometrics recognition systems on the market are equipped with sophisticated technology to detect the presence of an artificial eye and tell when they are being spoofed. The bottom line is that a quality, modern iris biometrics recognition system would not have been fooled by the re-engineered iris image used in the Black Hat conference paper.
What is rather unfortunate about the content of this article is that virtually no one who was exposed to the Black Hat Conference paper will have the opportunity to hear the points brought out by Daugman and will automatically deduce that iris biometrics systems should be avoided at all costs since they can be easily hacked and your iris template stolen. Daugman’s view will be known by few, fueled in large part by organizations like the Electronic Frontier Foundation who immediately pounced on the Black Hat conference paper and began their mission to spread the word that iris biometrics are just as susceptible to attacks as any other biometric modality, without reporting both sides of the issue.
We hope that you will take the time to educate yourself on the entire issue so you can formulate your own intelligent opinion when presented with all of the facts. Please share your thoughts with us on where you stand on the issue and why in the comments section below.












Hopefully the electronic frontier foundations has some success. Even if the iris code might be reasonably safe, it is not at all a good invention for a free and peaceful world. However, a mere engineer would not understand, though.
M2Sys was right to say that reporting of the Black Hat results should not overstate the problem. By the same token, advocates for biometrics should be careful with their balance too. For example, is it fair to say as M2Sys does that biometrics are “nearly impossible” to reverse engineer?
The point is not that iris scanning will suddenly be defeated left and right — the practical risk of spoofing is indeed not widespread nor immediate. But this work and the publicity it attracts serves a useful purpose if it fosters more critical thinking. Most lay people out there get their understanding of biometrics from science fiction movies. Without needing to turn people into engineers, they ought to have a better handle on the technology and realities such as the false positive (security) / false negative (usability) tradeoff, and spoofing.
My observation is that biometrics advocates have transitioned from more or less denying the possibility of reverse engineering, to now maintaining that it really doesn’t matter. But until the industry comes up with a revokable biometric, it is only prudent to treat seriously even remote prospects of spoofing.
I completely aggree with John Daugman’s view. I further believe that his views regarding the Black Hat conference paper should be widely disseminated across the globe.