What Role Will Biometric Authentication Play in the Post-pandemic World?
The global pandemic has fundamentally changed the way we live and work. To prevent the spread of coronavirus, scientists and industry leaders are looking for ways to leverage existing technologies to address novel problems. One of these technologies is biometric identification.
Biometrics, supported by machine learning development services, is already helping many organizations in their battle against COVID-19. Biometric scanners deployed in the workplace (or any crowded place) can identify infected individuals even before they feel the symptoms themselves. Moreover, biometrics can add a layer of security to organizational data that, due to widespread work from home arrangements, is accessed from different devices and locations.
What is Biometrics?
The first commercial use of biometrics dates back to 1858. William James Herschel, a British administrator in India, was in charge of building roads in Bengal during a time of unrest. Herschel asked local subcontractors to sign contracts with their fingertips so that he could track them down if they decided to abandon the job site.
Biometrics include an individual’s physical and behavioral characteristics; they are unique (even for twins) and can be reliably used as a means of identification.
Physical biometrics include fingerprint mapping, iris scanning, and voice recognition, among others. An example of behavioral biometrics is on-screen behavior, such as mouse movement and keystroke dynamics. Behavior biometrics even extends to the way each person sits and walks.
Biometrics in the Pre-pandemic Era
Back in 2018, enterprises already recognized biometrics as an effective method of enforcing security. According to the Ping Identity Survey, 92% of participants perceived biometrics as an “effective” or “very effective” way of securing the data stored on-premise.
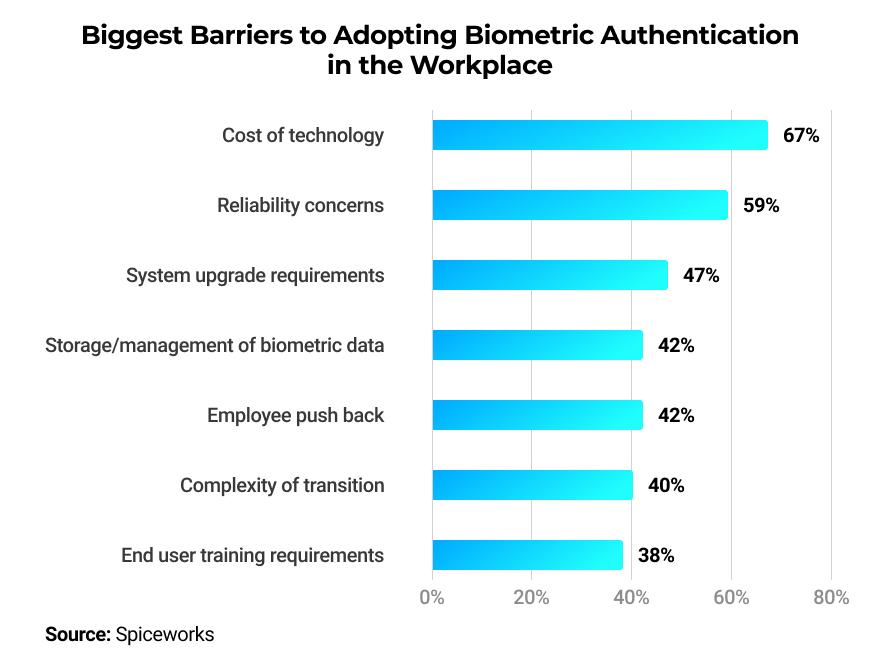
During the same year, Spiceworks conducted another survey revealing that 62% of responding companies already have some form of biometric authentication in place, while an additional 24% were planning to install such a system in the coming two years.
The participants that were delaying the use of biometrics cite technology costs as the main factor, followed by reliability concerns.
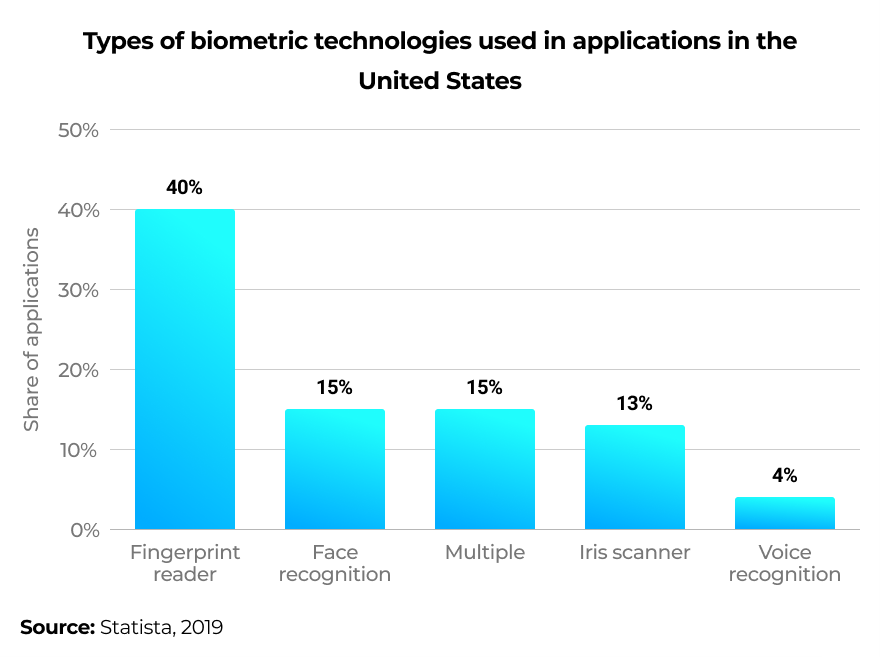
Multiple forms of biometrics are used by companies to secure access to their IT systems. In 2019, the most popular form of biometric authentication was fingerprint recognition.
How to Leverage Biometrics During the Pandemic
Biometrics can help resolve a host of pandemic-related problems, namely limiting the spread of coronavirus by identifying the carriers and enhancing authentication mechanisms in companies conducting business online.
Challenge 1: Limiting the Spread of COVID-19
Since the beginning of the pandemic, people have been searching for ways to minimize the spread of the infection. Identifying the carriers early on and isolating them plays an important role. Biometrics not only detect the potentially sick but also point out individuals who do not adhere to the safety measures, such as wearing masks and using hand sanitizer.
Sports Stadiums Use Facial Recognition to Detect Fans Neglecting Coronavirus Precautions
When sports activities fully reopen, stadiums will need a way to control the crowd and ensure all the necessary precautions are in place.
The Los Angeles Football Club is updating their virtual ticketing technology with biometric capabilities. It can already perform temperature scans and detect individual spectators that are not wearing masks. Upon entrance, every guest will be required to remove their mask for a facial scan.
European soccer clubs are hoping to follow the US lead and employ facial recognition systems too. However, European regulators are already concerned that such authentication systems could be an invasion of individual privacy secured under the General Data Protection Regulation (GDPR).
A Fire Department Takes Care of Firefighters with Biometric Rings
Employers are using biometrics to spot infected individuals at work and offer immediate help.
For example, the Duxbury Fire Department, Massachusetts, supplies its staff with biometric rings, which help recognize individuals who’ve contracted the virus. These rings track firefighters’ vital signs and sleep cycles to identify when they are the most susceptible to coronavirus (or any other disease). The data from every ring is analyzed and transferred to the corresponding firefighter’s smartphone.
Such rings cost $300, and the fire department is distributing the devices on a voluntary basis. The experiment has been a success, with 90% of the firefighters volunteering to try it out. As the Fire Chief Kevin Nord mentioned:
“I just wanted to give the men and women another tool to keep them healthy.”
Voice Recognition as a New Tool to Spot Infections
Another example is Sonde Health, a healthcare organization that is using voice recognition to identify infected healthcare workers. The solution employs machine learning to six-second voice samples to spot COVID-19 symptoms such as coughing, shortage of breath, and chest pain. David Liu, the CEO of Sonde said:
“At Sonde, we have unlocked voice as a new vital sign to enable secure, accessible, and non-intrusive monitoring of health.”
Challenge 2: Enhancing Enterprise Security
With the start of the pandemic, an overwhelming amount of the workforce moved to work remotely. According to a survey by Gartner, almost half of the participating organizations reported at least 81% of their employees are working from home, and 41% are likely to adopt the WFH policy for a longer period.
With this work paradigm, online resources and personal devices are heavily used, giving hackers an opportunity to interfere. The FBI’s cybercrime division reports receiving around 4,000 cybersecurity complaints a day, which is 400% of its 2019 volume.
As a result, enterprises are searching for more reliable ways of securing their data, especially when conventional passwords seem to work as an invitation for security breaches. Biometrics presents a convenient form of authentication, as people can’t lose or forget them, and they can’t be stolen or cracked.
Traditional Passwords Fail to Prevent Security Breaches
Even prior to the pandemic, passwords presented a weak spot in enterprise security. Even though they are easy to replace when compromised, they are also easy to steal, and sometimes even guess. Enterprise employees are facilitating hacking even further, as 99% of them are reusing their passwords across networks. A Verizon Data Breach Investigations Report showed that 80% of hacking-related data breaches benefited from lost/weak credentials.
Breach Examples
As WFH policies are now widely adopted by most organizations, video conferencing apps like Zoom have become commonplace. After a series of hacking incidents, 500,000 Zoom passwords were up for sale on the dark web for $0.002 per credential. As a result of this, some government agencies are requiring contractors to remove Zoom from devices they use for work.
In May of this year, Magellan Health was struck by a well-planned cyberattack. Hackers installed malware to intercept employee credentials and use them to access sensitive patient information. Around 365,000 patients were impacted.
Biometrics as a More Reliable Authentication Solution
As established above, biometrics play an important role in security, as they present a reliable identification solution. However, not all types of biometric authentication are in equal demand. For example, contact-based biometric systems placed in public spaces tend to scare people away. Consequently, ABI Research predicted the global biometric market to lose around $2 billion during 2020. This loss is mainly attributed to the reduced demand in contact-based biometric solutions.
According to Mohammed Murad, Vice President of Global Sales and Business Development at Iris ID:
“We feel very strongly that under the circumstances now and previously, in the majority of cases, customers do want something that is non-contact, accurate, and frictionless.”
However, this is not the end of contact-based biometrics. People are still comfortable using them on their personal devices such as PCs and smartphones.
Examples of Biometric Authentication
In 2019, NatWest became the first bank to issue biometrics-based credit cards, using the owner’s fingerprints for payment authorization. With this security measure, even if the card is stolen or its number is intercepted, the thief can’t initiate any transactions.
Barclays, an international banking chain, was among the pioneers employing voice-based customer authentication. When a customer calls, they are identified from the first few words of the conversation. This method protects the bank’s support team from processing fraudulent calls.
Privacy
For some users, biometrics are raising privacy concerns. Most of the time, authentication systems are not limited to collecting biometric data. They also capture where and when the person was at the time of scanning. People are aware that companies store their biometric data, but they don’t know how secure it is, or if and how this data is being processed. Some might find later that this data was used without their permission on “side projects.”
Two Illinois residents filed a lawsuit against tech giants IBM, Amazon, and Microsoft for using images of their faces without permission to train a facial recognition system. This violates the Biometric Information Privacy Act, which was passed in Illinois over a decade ago. Earlier this year, Facebook paid $550 million on a lawsuit stemming from the same regulation.
Privacy concerns related to biometrics are particularly challenging for enterprises operating on an international scale as they might need to transfer biometrics across geographical borders. In this case, it is essential to understand privacy laws in your location of operation. To reduce the risk, store and process all biometric data on one local device. This practice will also reassure your employees their data will not be maliciously accessed as it can be with the cloud.
The Future of Biometrics
Thanks to advances in machine learning, biometric authentication is gaining reliability. Researchers are investigating the possibility of adopting behavioral biometrics and are coming up with new authentication modalities. Moreover, there are studies on privacy-preserving technologies such as zero-knowledge cryptography that enable secure storage of biometric data.
Experts predict that in the future, biometrics might be used in combination with password-like credentials. This is especially convenient for enterprises with locations in different parts of the world. These companies can use passwords when accessing resources across borders to mitigate issues related to GDPR and other legislation that prohibits transferring biometrics.
Continued intensive research will make biometrics even more secure in the future. However, if a company uses a weak, outdated system and user biometric data is breached, it will be a challenge to recover as biometrics are forever linked to a particular individual and can’t be easily replaced like passwords.
Getting Started with Biometrics
Biometrics was in use even before the pandemic due to their convenience and reliability, and they are even more relevant now, as many business transactions occur online.
Before deciding on the best fitting biometric recognition method for your facility, think about the following aspects:
- Identify the type of authentication you already have and what you can replace. If you installed an access card system, maybe it is best to replace it with a touch-free biometric recognition technology so that employees who often lose or forget their cards will still have access.
- Decide whether you want to employ a one-factor-authentication or prefer a multimodal approach.
- Make sure you guard your employees’ privacy and be careful with storing and using biometric data.
- Check how your approach to biometrics corresponds to the legislation in your country.















